IoT Regulation is coming, and cybersecurity will be the key focus
We are moving toward a fully digitalized and connected world. The way we work, the way we communicate, the way we interact with our ecosystem…is changing.
This is also becoming the reason why companies that were typically analog and ‘offline’ (in terms of connectivity), are now becoming Internet companies. The IoT era will bring many advantages, but also risk and security issues that are inherent to having everything connected.
The threat is real. Several examples in the past years have demonstrated how vulnerable a system can be when security issues become ‘the elephant in the room’, always there but with nobody willing to tackle the issue:
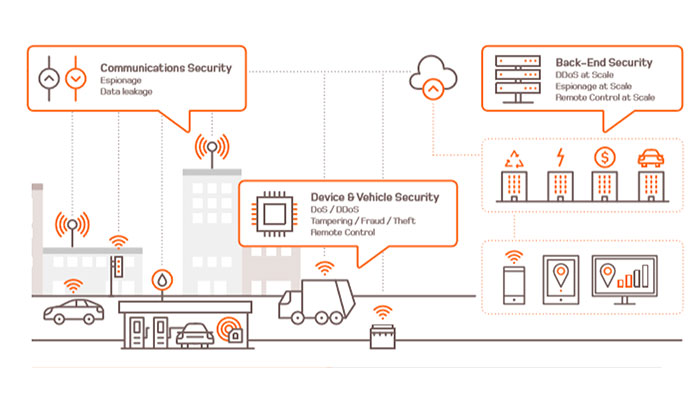
- Personal data leaks. Many of these IoT devices stored data related to our health, energy consumption or geolocalization; a lack of proper security mechanisms allows access to this information by unauthorized agents. [The Roomba case (New York Times)].
- Critical infrastructure attacks. Factories, power plants and industrial facilities alike have exposed some of their devices and control systems to the outside world – as we have seen through Shodan [1]– but, also, the deployment of connected devices inside the industrial networks has broken its principle of isolation. [The infected Smart Coffeee Machine (Tripwire)].
- Economical losses. Security incident have a direct or indirect economic impact. A good example is the DDoS attacks which may cause that different online services are temporarily not available. These attacks are now amplified because of the high number of unsecure IoT devices [The average DDoS attack cost for businesses (ZDNet)].
- Safety in danger. The connectivity is also arriving to automotive, rail or aerospace sector where security was never a problem in mind, now it should become crucial to avoid safety risks. [Tram network hacked by a teenager (The Register)].
Most of these problems are not new (e.g. DDoS attacks have been always there) but they get to be magnified thanks to the number of IoT devices can be found outside. By incorporating all kinds of IoT devices, the attack surface of any system becomes larger, and the existence of weak links more prone to be exposed and identified. Imagine what could be done with 30.7 billion devices predicted by 2020 being part of a massive and malicious bot net.
The lack of regulation and standardization regarding IoT security has helped to reach this situation. Also, the lack of proper security awareness from IoT developers, many lessons learned on other IT areas (importance of secure communications or strong authentication mechanisms) seems to be forgotten when we reach the IoT ecosystem.
IOT Regulations in Europe and USA
However, this may change in the short term. Most governments, especially in Europe and USA, are worried about this absence of security. In Europe, IoT devices handling personal data should protect their integrity and confidentially, both at rest and transit, according to the European General Data Protection Regulation (GDPR). The lack of a proper update mechanism could be a real headache if your company is under the scope of the Network and Information Systems (NIS) directive (think of IoT devices for Industry 4.0). It is true that the above mention regulations were not directly thought to tackle IoT, but they have major implications for IoT solutions.
In the USA, the state of California has passed the SB-327 Information privacy bill into law. It is the first regulation for IoT security in the States — I would say for any western country. This will stop bad practices, such as the use of insecure default passwords within IoT devices sold in the state of California from January 1st, 2020. The first real milestone towards regulating IoT security.
Furthermore, cybersecurity is becoming a main concern for several safety-critical industries such as automotive, aerospace or healthcare. As those industries connect their operational systems, security risks are turning into safety risks and can no longer be avoided. Some regulation initiatives for those sectors are being discussed right now, such as the SPY Car Act or the Medical Device Cybersecurity Act in the USA, or a commission for drone cybersecurity requirements in Spain.
Developing a security certification scheme for IoT solutions can be an answer to asses compliance with the requirements of the future (and present) regulations. However, there is still no adequate security certification scheme for IoT. There are two main reasons: The first one is that current schemes such as Common Criteria (CC) do not fit well with the time to market demands of most IoT products – good high assurance security certification but not as lightweight option. The second is the huge range of products that fall under the name of IoT (connected cars, drones, smart meters) that will require a specific certification process for each of them. The upcoming European Certification Framework may be able to solve both issues.
IOT Cybersecurity guidelines and recommendations
In the meantime, several guidelines and recommendations have been published to help IoT developers understand and improve the security of their solutions:
- ENISA – Baseline Security Recommendation for IoT
- UK Government – Code of Practice for Consumer IoT Security
- NIST – NIST initiatives in IoT
- OWASP – OWASP IoT Project
- GSMA – GSMA IoT Security Guidelines/Assessment
Applus+ IT laboratories can help you check the compliance with any of these guidelines or give you technical support to improve the security of your IoT Solution. Our experts can support you from the very conception of the product (threat model, risk assessment) through product development (training, source code review), product testing (vulnerability analysis and pentests) and certification (official certification scheme, such as CC or private security assessment).
More Info about Appus+ Laboratories cybersecurity evaluations for IoT.